
Table of Contents
ToggleBefore we go into the vast paths and trails we have planned for today, let’s start by imagining that we were unwittingly introduced into a SAW or “Fermat’s Room” type movie, where we are locked in a location with different people, both known and unknown to us.
Given this, we are presented with the premise that either we solve certain mathematical games/puzzles in order to survive, or we will end up in a catastrophic ending.
Therefore, we must cooperate with each other, since by joining all the ideas or solutions we have about the challenges, we will be able to move forward to escape from a cruel destiny.
In this situation, all the messages we are given game after game complement each other and give us more information, either about the other people around us or why we are there.
In the end, all our efforts come together and, although some win some and others lose some, we receive as an incentive to continue with our lives and corroborate the assumptions we have.
In a similar way, but less bloody and terrifying, is how the Proof of Work system works, so get ready, because in this article we will talk about mining, what this interesting mechanism consists of and its origin.
What is Proof of Work (PoW)?
Proof of Work or Proof of Work, “PoW” for short, is one of the most widely used consensus algorithms for cryptocurrency mining, as is Proof of Stake (PoS).
Its function is relatively simple: to avoid double-spends (double spending, better understood as duplication or use of the same currency in two or more different transactions) by verifying and recording transactions securely.
To this end, it makes use of the hash function, which is a type of cryptographic function that makes use of mathematical functions to encode the information exposed in blockchain technology, ensuring that it is authentic and unique, resulting in a valid hash.
It is irreversible in nature and each hash of the block, encrypts the data of the previous block and so on throughout the blockchain.
In short, proof of work is achieved when certain computers or mining machines solve a complex mathematical problem and are rewarded by adding a block (with transactions inside) to the blockchain.
These mathematical problems have the particularity of not having an “efficient” way to be solved and that is why miners have to find the answer to the problem by trying combinations.
To perform more calculations they need more powerful equipment and that is why you may have heard that energy-intensive mining rigs are needed.
How did it all start? The history of PoW
Let’s go back to the 1990s, where, although computers didn’t have half the functions they have today, they were a brutal technological revolution.
As early as this decade, in 1992, we began to talk about both security and spam or malicious mail, and this was noted by computer scientists such as Cynthia Dwork and Moni Naor in their article “pricing through processing or fighting spam”, who argued that, to deal with a wave of fraudulent e-mail and other associated problems, a user was required to calculate a moderately difficult, but not intractable, function.
Does this sound familiar? Yes, it does! It’s like the example I was giving you of SAW and Fermat’s room, where, to rectify suspicions about your roommates and clarify doubts (in this case, the concern is whether an email is fraudulent or is spam), we solve riddles.
This is undoubtedly the whole basis of the proof-of-work system, since its function is that one party, called “the prover” or the demonstrator, proves to the others (verifiers) that a certain amount of specific computational effort has been expended.
Therefore, verifiers can confirm the expenditure with minimal effort on their part. This concept was invented by the aforementioned Dwork and Naor in 1993.
However, the term “proof of work” was only used and formalized in the 1999 article by Markus Jakobsson and Ari Juels, computer security researchers and writers.
Now, with the idea in mind of what Cynthia Dwork and Moni Naor were commenting on in their article, there was an essentially important mechanism that was presented many years before the Bitcoin white paper, known as Hascash.
Hascash is a type of proof-of-work system that was proposed in 1997 by Adam Back and, more formally described in the article “Hashcash: a denial-of-service countermeasure” by the same author in 2002.
Simply put, in e-mails, a textual encoding was added to the header of an e-mail to show that a certain amount of time was spent in generating it, so its sender was not a spammer.
This mechanism, for the first time, demonstrated that a proof of work worked quite well in reality and opened the door to the development of PoW systems in other scenarios.
Later, in 2008, Satoshi Nakamoto made the Bitcoin protocol public in an article, where he established Proof of Work as a key aspect of its functionality, which eventually made the PoW algorithm very popular.
Currently, several projects such as Bitcoin Cash, Bitcoin, Ethereum, Litecoin and other cryptocurrencies use proof-of-work, mainly for its contribution to competitive mining.
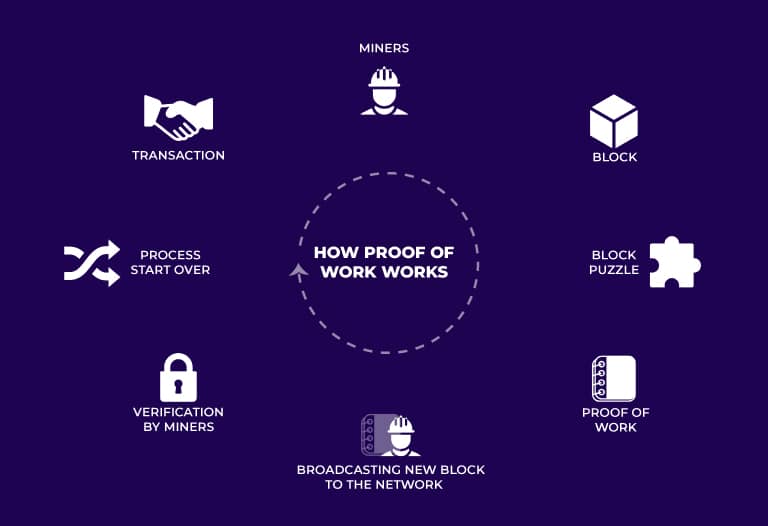
How does it work?
To understand how the proof of work works, I will break it down into five phases:
- The participants of the network or node establish a connection with the network, who assigns them a computationally complete task or puzzle, which must be solved in order to receive an incentive (reward in cryptocurrencies). In the case of SAW, it is the test presented to us that we must solve in order to survive when we encounter Jigsaw.
- We begin to solve the horror movie riddle or mathematical problem, which, actually, must be solved by certain computer equipment (varies according to the cryptocurrency) characterized by a certain power.
- Once finished, the miner or participant shares his or her result.What in SAW is the call to action to get out of some machine or situation.
- Subsequently, the solution is checked to ensure that it meets the system requirements and if it does, access is granted. If it does not, access is denied and the solution is rejected, which, in movies, leads to a complicated outcome. Double-spending protection is also checked here.
- Once it is confirmed that the problem was successfully cracked, the user or miner accesses the network resources and receives their incentive which would be cryptocurrencies or, in our thrillers, the completion of a horrible experience. At this point, one particular hash can be obtained that encodes the whole process.
What are the advantages and disadvantages?
Advantages
From everything we have reviewed, we have observed that it is a very secure process. Miners receive the bounty in exchange for contributing their computing power to the blockchain network. This makes it more difficult and costly for someone to attack these blockchains.
In addition, PoW generally provides greater decentralization to any network.
On the other hand, it has a good defense against DoS (Denial of Service) attacks, so it would not start rejecting requests due to the “low capacity” of response that it could present in the face of all the demand.
Disadvantages
Because of the increasing difficulty of the puzzles presented by the readjustments that the system may have when considering the response times of the puzzles, more and more powerful and highly specialized hardware is needed.
Additionally, they consume a lot of power and are vulnerable to 51% attacks, or wholesale attacks, on small proof-of-work chains, meaning that one user or a group of users have enough power to control what happens inside the network.
Glad to see you made it this far!
I know this has been an information-packed article, but we hope it has been very useful to understand a little more about how the wonderful crypto ecosystem works.
But…oh…wait, you were left wanting more?
Don’t worry! At Bitnovo, we are working hard so that you not only have the best information at your fingertips and in less time than a rooster crows on our blog, but we also have our own website where we bring you closer to the world of cryptos in an easy, fast and secure way.
Are you ready to take action? Perfect, see you on Bitnovo and on the blog in a new post.




