
Table of Contents
ToggleBlockchain technology is often associated with decentralization and security, without a decision center and control bodies that can be attacked or corrupted, making decisions against the rest of the network.
In fact, the Blockchain can be defined as a peer to peer system, where nobody has privileges.
So, what is a 51% attack on the Blockchain? Is it possible to attack and enter the network of this extraordinary technology?
What is the 51% attack: definition
A majority attack (usually called a 51% attack or attack > 50%) is an attack that occurs on blockchain networks using the consensus mechanism of proof-of-work (PoW).
The Proof of Work, or mining, is the first consensus method used by cryptosystems such as Bitcoin or Ethereum and is also the consensus method most vulnerable to these attacks.
In the case of cryptomonies that use mining or Proof of Work (PoW), 51% of decision makers translate into 51% of mining capacity, and more precisely into the ability to calculate hashes.
Although the main blockchains are very resistant to these types of attacks, the smaller cryptomonies are very vulnerable, as there are few people involved in mining.
Photo Credits: Linkkoin.com
Thus, a 51% attack occurs when a person or group controls 51% of the network’s computing power. In other words, it would have more computing power than all other miners and voting participants than the rest.
An example of what someone can do with 51% of the network is the double-spending attack: a payment is sent with a transaction, just before it starts mining blocks in secret. The transaction is validated by the entire network and arrives at its destination, with the payment being accepted as such.
Once what has been purchased has been secured, the attacker makes public the chain of blocks he has secretly extracted (so-called shadow mining).
Having 51% of the network, that blockchain will be validated by the rest of the network, in some kind of consensus or democratic process. After acceptance, the transaction that took place immediately afterwards will disappear and the payment money will return to the attacker, who will be able to spend it again. In addition, all subsequent blocks will be rewritten, in what is known as deep chain reorders.
A 51% attack would probably not completely destroy bitcoin or other blockchain-based currency, even if it was very harmful.
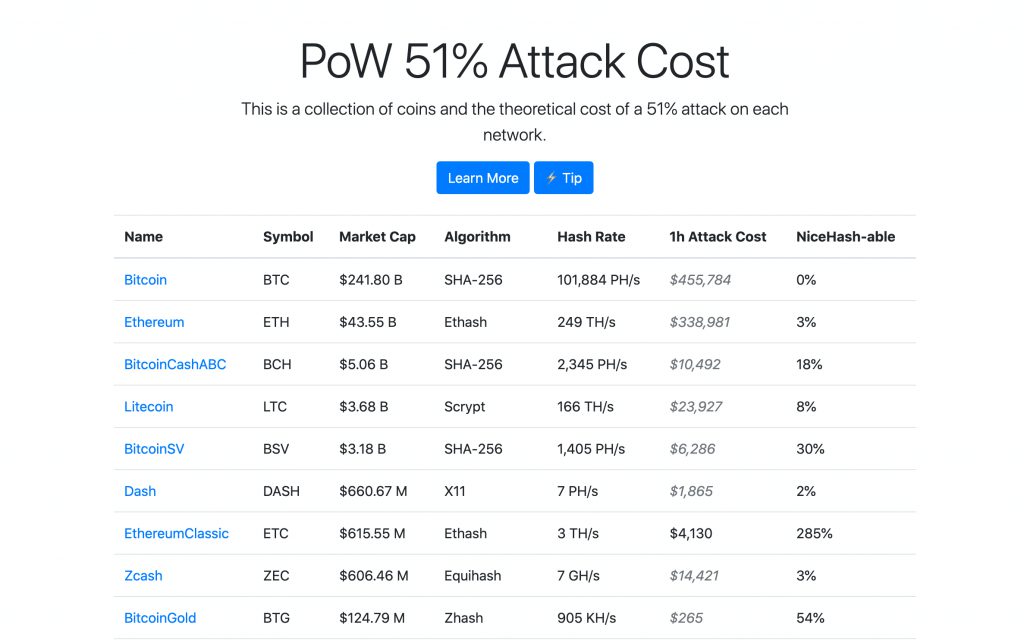
The Crypto51 page calculates the dollar costs involved in controlling the 51% network of some crypto-currencies that work with Pow (PROOF OF WORK).
How does a 51% attack work?
Bitcoin and other crypto currencies are based on the blockchain, a chain of blocks and a distributed ledger form. These digital files record every transaction made on a crypto-currency network during a specified period. For bitcoin, a new block is generated approximately every 10 minutes. Once a block has been completed or extracted, it cannot be changed, as network users would quickly detect and reject a fraudulent version of the public ledger. As a result, no one can spend a coin twice.
However, if an attacker or group of attackers control most of the computing power of the network, they could interfere with the process of registering new blocks.
For example, they can prevent other miners from completing blocks, which theoretically allows them to monopolize the extraction of new blocks and earn all the rewards.
In the case of bitcoin, a 51% attack could block the transactions of other users and could send a transaction and then cancel it, making it appear that they still have the currency they just spent. This vulnerability is known as double-spending and occurs when someone can spend the same token several times. This is the digital equivalent of a counterfeit.
A network that allows double spending would quickly suffer a loss of confidence.
Changing the historical blocks, i.e. the transactions that were blocked before the attack began, would be extremely difficult even in the case of a 51% attack. The further back the transactions are, the more difficult it will be to change them.
On the other hand, a 51% attack is possible with less than 50% of the network’s mining power, but with less chance of success.
Examples of blockchain platforms that suffered a 51% attack
Let’s see below some real cases of 51% attacks against some networks and crypto-currencies.
Bitcoin Gold: In May 2018, Bitcoin Gold, one of Bitcoin’s forks, and at that time the 26th largest cryptomat, was attacked by 51%. The malicious actors controlled a large amount of Bitcoin Gold’s hash power and were able to spend twice over several days, stealing over $18 million due to the double spending.
Verge was attacked at least twice, the first and most serious attack in early April 2018. Because Verge’s supply is not limited and new tokens can be extracted, the attacker issued new Verges worth more than $1 million. As a privacy-centric currency, the identity of the attacker is very easy to conceal.
Ethereum Classic double spending reached $5.6 million.
Vertcoin was attacked in November 2018. One or more attackers took control of the hash power and stole approximately $100,000.
Krypton and Shift, two ethereum-based blockchains, were attacked by 51% in August 2016.
The probability of a 51% attack occurring
Beyond the real-world examples, due to the enormous hash power in the Bitcoin and Ethereum block chains, it is not theoretically and economically feasible to carry out a 51% attack. In fact, it is estimated that a malicious miner would need computer power or hash power to replace that of millions of miners worldwide and would have to spend an enormous amount of money to acquire mining hardware that can compete with the rest of the network.
However, that does not mean that there are no other ways to initiate 51% attacks. An error in the code of a block chain could, in some cases, open the door for a miner to produce new blocks at a much faster rate and start a 51% attack.
This is why these attacks are common in smaller working test block chains, as less computing power is required in this case.
History shows us that the Bitcoin block chain has never suffered a 51% attack, also because it has an active hash power that is difficult to compromise.








