
Table of Contents
ToggleRemember those sci-fi movies or series, like Psycho Pass, where they have those cool houses with state-of-the-art technology and holograms all over the place?
A complete dream, isn’t it? But now imagine that a thief wants to break into our house to take some of our belongings. Seeing that everything is completely technological and some things are holographic (but they allow you to keep things inside), he ventures to try.
But, oh, surprise! As soon as he tries to take an object, everything automatically changes order. The cute little vase in the living room is now in the master bedroom and every time she tries to take something, the same thing happens.
It’s like when our parents constantly moved the chocolate stash as soon as they saw that there was one less chocolate in the bag, but automatically.
In a similar way, we can visualize and understand secure hashes or, as I call it, Bitcoin’s anti-theft method.
Let’s review what makes it so fundamental to the Bitcoin Blockchain and many cryptos and what is the reason it is one of the most secure algorithms within the crypto ecosystem.
What is a Hash Chain?
A Hash Chain, also called a Hash Chain, is a sequence of values that are produced by the consecutive application of cryptographic hash functions on a specific block or blockchain.
Recall that the hash function is a cryptographic function that encodes an amount of input data from a blockchain (which is equivalent to a correct or valid hash).
The purpose of this is to generate a unique string of characters that represents, numerically, all the data found in that block. That is, instead of “Alice sent 5 btc to Louis” it would be “DFCD3453”.
Certainly, it is unidirectional, because it cannot be reversed after the hash of the block has been confirmed. In other words, it is virtually impossible to access the original data. If the information is modified, the code that was generated is changed.
Basically, a hash chain replicates this process a large number of times until a complete block chain is completed. Consequently, it is like a Merkel tree or a Hash tree but with a single branch or line.
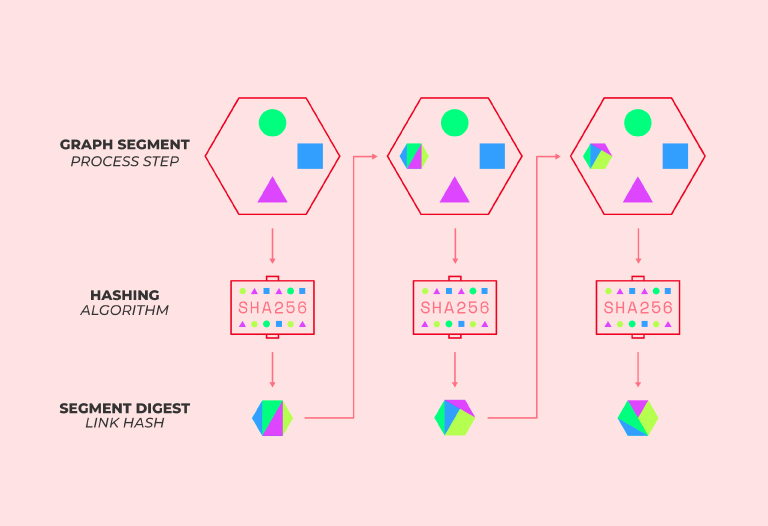
How does it work?
To understand how this goes, let’s imagine that we are making use of the blockchain technology of some project. It could be Satoshi Minamoto’s Bitcoin, Vitalik Buterin’s Ethereum or whichever one strikes your fancy.
The first thing you must do is to provide some input data in the first interaction or session you open to make the transaction.
This first information is encoded by a hash function such as the SHA-256 hashing algorithm, which will result in a code with a fixed length that helps authenticate the next time you enter your data in a second session.
In this way, that output (the resulting code) is like a fingerprint that identifies the input and the files.
Over a set of sessions, these individual hash entries create a hash chain that further validates a user’s input.
After that, if everything is valid, the transaction will be carried out and registered.
What are its uses?
Authentication in blockchain
As described in the previous section, all the processes it runs have the function of authenticating the entries with previous hash keys.
These types of hash chain processes are widely used by Bitcoin and other cryptocurrencies.
One time passwords
This “method” or sequence is typically used to produce single-use keys from a single key and the keys are used in reverse order of generation.
In other words, with one key, many keys are created and the first one is the last one to be used and vice versa. Each key can be used only once, which reinforces security.
This use became popular thanks to the suggestions of Leslie Lamport, a computer scientist known for his contributions to various theories and algorithms such as Byzantine fault tolerance and for being the creator of the LaTeX word processor.
Detection in virus scanners
Hash functions are like fingerprints, which is why they are often used in it to detect possible modifications to a file.
It is also useful for identifying damaged files, as this type of data produces a different output, which makes it easier for specific software to find.

So much for our journey.
If you are interested in reading more articles associated with the news of the crypto universe and its basic concepts, you can click on the topics below or go to our blog. We know they will be totally useful for you.
For the time being, see you in a future article!








