
Table of Contents
ToggleDo you remember the typical marriage scene between the protagonist and her leading man in a soap opera or movie, where, out of nowhere, the audience says “I object” and then the course of the story changes completely? Byzantine faults work in a very similar way.
Although, of course, in those cases, the protagonist decided who to stay with, despite the defects that each one had, finally reaching an agreement with both parties to end in an ending typical of a Disney film production. It is at this point, where we will focus and begin to talk about Byzantine fault tolerance, a computer system that, although it is not as romantic and fantastic as a love movie, it is an ideal and widely used solution in the blockchain technology of cryptocurrencies.
What is Byzantine Fault Tolerance (pBFT)? Let’s talk about consensus algorithms
We can define it as the ability of a distributed computer system to reach sufficient consensus and function properly, despite malicious components or bugs (nodes) in the system that fail and disseminate incorrect information. In other words, it is an appropriate consensus protocol to avoid catastrophic system failure. A practical example would be to avoid believing the hearsay of our neighbors and to try to maintain an objective point of view on the information of one person or another.
Currently, we can find different projects that use the practice of Byzantine fault tolerance: Hyperledger Fabric from the Linux Foundation and Zilliqa, an Asian project recognized for its crypto ZIL.
Indeed, the term “Byzantine fault” and “Byzantine fault tolerance” derives from the problem of Byzantine generals, which, within technology and computing, is a well-researched and complex dilemma, despite its easy sounding history.
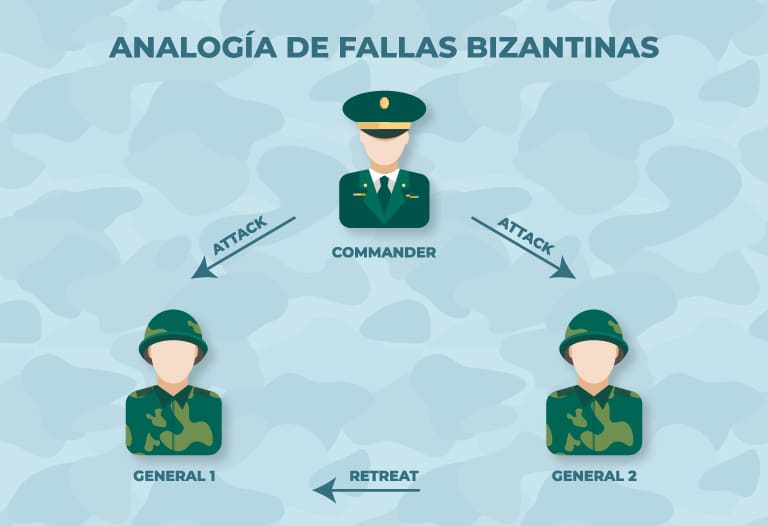
The dilemma of the Byzantine generals
During war, generals must decide whether to attack or retreat in the face of the enemy. In such a situation, there is no shortage of generals who prefer to attack and give their hearts to the end, while others prefer to retreat. Clearly, the important thing is to reach a common agreement, since a disorganized attack ends in defeat.
The problem lies in the presence of spies or traitors, as in Among Us, who will look after their own interests. To understand this, let’s imagine ourselves in this situation: we are nine generals of the Spanish armed forces and the concern for our enemies is increasingly latent, so we decide to hold a meeting to vote on what we will do: attack or defend ourselves.
Of the nine of us, four agree to withdraw and four agree to attack. The decision rests with that ninth general, who may be a traitor. This is where the problem lies, since he has the absolute decision: we attack or we retreat.
Now, to this we can add another communication problem and that is that we think that physically we were not together, but we decided to send letters with our decision, which can be forged or not delivered by the messengers. In these circumstances, as a possible solution, is where Byzantine fault tolerance acts. But let’s go deeper into this in the next point.
How does Byzantine Fault Tolerance (pBFT) work?
Returning to the previous example, faced with the problem of traitors and messengers who may withhold or distort information (in other words, a Byzantine fault), tolerance of Byzantine faults would establish a system with consensus mechanisms that ensure that traitors cannot lead to a fault.
Thus, it ensures that the loyal generals can have a majority agreement and avoids that, in the case of the Oscar-worthy marriage, the protagonist and her handsome suitor are separated. Certainly, for this, rules must be defined by the system.
Let’s get to know the most common rules within Byzantine fault tolerance. Imagine that we are in a mining process and we want to perform a transaction on a blockchain, using a Byzantine fault tolerance method. In that circumstance, we will observe four phases:
- As users who are performing the transaction, we send our confirmation request to the main network node. However, considering that the first rule is to initiate in an undecided state, the transaction on the blockchain will not be confirmed for the time being.
- The main node will transmit our request to all the secondary or backup nodes, so that each one can verify it and include it. In this instant, remembering the example, the system is guaranteeing a secure means of communication of the information.
- After the information has been disseminated and verified, the nodes begin to evaluate whether or not the transaction is valid, thus moving to a decision state.
- Finally, the nodes, based on their evaluation and verification that each decision was the one issued by each node, perform the service that was originally requested (confirmation of the transaction), culminating the process with the authorization of the nodes on the validity of the transaction.
What are the advantages and disadvantages?
Starting with its advantages, pBFT does not need multiple confirmations, nor a waiting period to ensure that a transaction is secure or valid after it is included in a block, since it is done quickly.
Apart from that, it can reach consensus without requiring excessive energy usage for miners, ensures efficient network communication and reduces reward variation for miners.
However, it has some disadvantages. Among them, we can find that they are vulnerable to Sybil attacks, which are executed by the same entity that controls the network entities and corrupt the system. Additionally, it does not scale properly, since there is an overload of internal communication, so it takes time to respond to a request.
Undoubtedly, in the context of cryptos, it is essential to have a secure, efficient and fast system for the execution of transactions and other procedures characteristic of a blockchain.
Therefore, Byzantine fault tolerance has established itself as a good option and an attractive proposition compared to other algorithms such as PoS (proof of stake), PoW (Proof of Work) consensus and Pol (Proof of Importance).
Congratulations on making it all the way to the end!
From the Bitnovo team, we want to “reward” your interest in this article, so, as a symbolic gift, you will have access to the latest Bitnovo blog, completely free and without expiration date, so you can continue to be informed about the latest news on cryptos from the best writers on the subject.
In the underlined link you can review all our content!
For the time being, see you in a future article.



