What is cryptocurrency? The basis for the birth of cryptocurrencies

Table of Contents
ToggleThe protection of information has always been seen as a necessity, whether for security or simply for privacy reasons.
Since World War II, a war more technological than World War I or the Cold War, the coding part of the orders was elementary..
Because of this, beyond the military confrontations and operatives, there were actors who conducted their own battles to discover the next enemy moves. More or less like Battlefield or chess, but more intense.
Consequently, whether as engineers or spies, their main mission was to decipher the enemies’ coded message.
Even in the times of Julius Caesar, a Roman military man, they were carried out in simpler but more cunning ways.
An example of this is the Caesar cipher, which consisted of shifting one letter (ex S) to the third letter following it ( ex V). Obviously, this was intended to protect messages with important military content.
Given this, we see that coding efforts have existed since ancient times. Of course, they have become increasingly refined, especially now, in a fully digital age where most processes are done over the Internet.
Hence, how fundamental is one of the most key concepts in the cryptocurrency scenario: cryptography.
Buckle up, because today we’ll take a brief tour of what cryptography is and how it works.
What is cryptography?
Cryptography is the process of converting text or a specific action ( ex. Transactions) to a result that is intelligible to an unauthorized person or system.
In other words, it is a method of storing and transmitting data in a particular form, the purpose of which is that only the recipients can read and process it.
It is mainly based on mathematical algorithms and computer science practice. Additionally, it has different utilities, such as protecting data from theft or alteration and authenticating users.
Its major contributors were Claude Shannon and Warren Weaver, who, in the 1940s, proposed the theory of information, which, in short, explains how information transmission and processing works.
In the universe of cryptocurrencies, this technique has been the essential basis for providing them with a decentralized, secure and anonymous nature. Indeed, because it encodes and decodes data on a network without requiring a central authority ( a bank).
This can be done by means of hardware or software, such as the protocols or algorithms we know today.
What is cryptography used for in cryptocurrencies?
Modern cryptography deals with four aspects:
-
- Confidentiality: The information cannot be understood by anyone who is not included in the process.
- Integrity: The information sent cannot be altered.
- Non repudiation: provides assurance to the recipient of a communication that the message originated from the sender and not from someone impersonating the sender. It also prevents the sender or originator of the message from claiming that he did not send the message.
- Authentication: The sender and receiver can confirm each other. That is, they can ensure that they are real users and not machines or fraudsters.
Therefore, the above aspects are aimed at:
-
- Ensure the security of transactions and participants occurring within the network.
- To protect possible double expenses.
- Verify the transfer of digital assets and tokens.
- Control the transfer of digital assets and tokens.
How does it work?
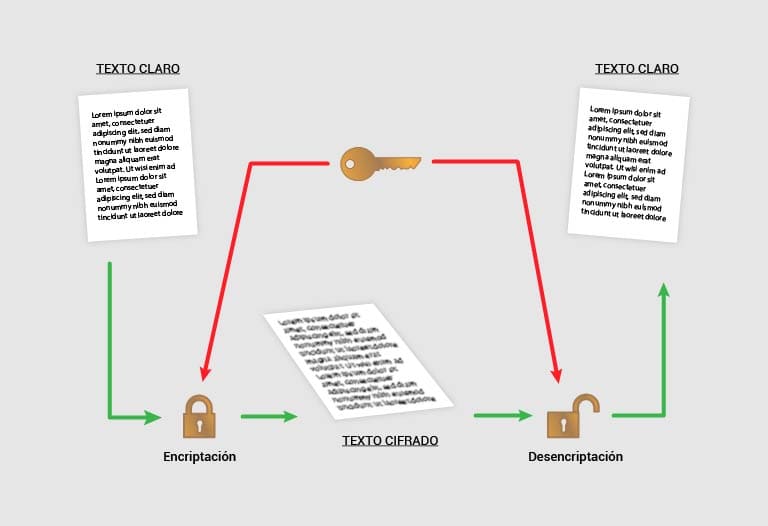
Simply put, encryption can be reduced to three processes:
-
- The sender encrypts or hides a message using a key type.
- This encrypted message is then sent to the receiver.
- Finally, the receiver decodes it to generate the original message.
In a real case, let’s imagine that a policeman is called to a crime scene. In order to report the situation to his superior, he will do so by means of codes or ciphers preestablished by them.
By using them, you are encrypting the message, so that only those who know that language will understand it.
After the message is communicated via cell phone or telephone, the superior receives the report. With his prior knowledge of the language used by the police officer, he understands the message (deciphers it) and indicates his role at the site.
As we can see, in cryptography, the secret key is the most essential, since they make the message or value unreadable to a reader or recipient.
Therefore, if we are people who have nothing to do with the police, we will not understand what they are referring to. In this way, the information remains secret.
Now, there are several cryptographic systems, so there is a wide range of possibilities of use within cryptos.
Types of cryptography used in cryptocurrencies
In general, three types of cryptographic techniques are used.
Hash functions
In previous opportunities, we have been able to delve deeper into what hash functions and hash chains are, initially, Bitcoin’s own.
However, broadly speaking, it is an algorithm that does not use any secret key.
For this reason, its objective is to encrypt the transactions of the previous blocks, based on a fixed length of text. Through this encryption, it becomes impossible to retrieve the unencrypted content.
This type of method is widely used for mining.
Symmetric or private key cryptography
This technique consists of both the sender and the receiver sharing a single key (symmetric keys), just like the communication process of one policeman with another.
Thus, the sender uses this key to encrypt his message and send the ciphertext to the receiver.
Once the ciphertext arrives at the receiver, apply the same key to discover it.
It is relatively simple, but it has its disadvantages, since:
-
- It requires that the sender and receiver have a prior agreement on the key to be used.
- If there are many operations, the number of keys to be memorized are numerous.
Public key cryptography
Also called asymmetric cryptography, it is a method proposed in 1976 by Whitfield Diffie and Martin Hellmon. Its purpose is to solve the disadvantages of symmetric cryptography.
To do so, they use two types of related keys: public and private keys.
- The public key can be freely published and is used for message encryption. Consequently, it would be like Morse code. Everyone can learn to use it because the way messages are encrypted is known.
- However, to decrypt the message, a private key is used, which remains secret so as not to compromise the confidentiality of the messages.
To give another example, it is as if you want to send a message to your friend Alexander. To encrypt it, you will make use of a public key (Caesar code).
However, to decrypt it, you will have to use your own key or a key generated and agreed upon by both of you.
The last two types are used to generate digital certificates of a transaction.
Therefore, the keys are very similar to a digital signature that allows securing a transaction.
So much for our journey.
If you are interested in reading more articles associated with the news of the crypto universe and its basic concepts, you can click on the topics below.
If you want to join this amazing cryptocurrency adventure, you can go to our home page and check our services.
Our support team will always be ready to answer your questions and help you with whatever you need.
See you next time!



